DBA News
-

Raspberry Pi KVMs compared: TinyPilot and Pi-KVM v3
If you have regular nightmares about driving 40 miles to push a power button, perhaps you should consider what a Raspberry Pi remote KVM device can do for you.
-

Abusing Smart Contracts to Steal $600 million: How the Poly Network Hack Actually Happened
An attacker discovered an exploit in the Poly Network cross-chain integration which allowed him to siphon off over $600 million in funds. Kraken Security Labs broke down how it all happened. Unlike most heists, there’s a happy ending for all parties.
-
Mental Models: The Best Way to Make Intelligent Decisions (~100 Models Explained)
Whether you’re navigating professional or personal life, you’ll find others think differently. Not talking opinion, but using entirely different frameworks. Being able to assume these other modes of thought will help you in surprising ways.
-

Google Cloud still promising Ice Lake Xeon VMs this year
Google is lagging behind Microsoft, Oracle and Amazon as the tech giants slowly update their data-centers and begin offering their back-office application and Web Hosting services on VMs powered by the new generation of Intel server processors.
-

Coding Dojo Partners with The Prison Scholar Fund to Train Formerly Incarcerated Individuals
Understandably wary employers reflect US prisons’ dystopian state as criminal colleges, in part causing a recidivism feedback loop. Many clever convicts are desperate to break that loop. Jury’s out, but hopefully we’ll do some redeeming in the US for once.
-

Remote work is widening the skills gap, report finds
Articles like these seem like the mirrored, corporate perspective on a thriving tech labor market, flush with advancement opportunities for IT and software professionals. Muster your discipline and ambition, learn some new skills, and carpe diem!
-

As tech unemployment plummets, executives reassess IT priorities
With an unemployment rate well less than half the national average, skilled IT professionals are in high demand right now as companies scramble to gather the talent necessary to complete planned IT infrastructure modernization projects.
-

Apple refuses to reinstate Epic’s ability to market or support Apple’s iOS and macOS hardware
From Tim Sweeney’s Twitter, Apple refuses to reinstate Epic’s ability to market or support Apple’s iOS and macOS hardware until all appeals are exhausted or Epic submits and kisses Apple’s ring.
-

How PCI-Express works and why you should care? #GPU
Knowing how GPUs mounted in PCIe slots work is important for troubleshooting and understanding the logistics of parallel processing. This is a great overview that is well worth the effort, but make sure you understand the OSI model before tackling it.
-

What is the Matrix?
Matrix is an open standard for interoperable Instant Messaging and VoIP allowing users with accounts behind Tech Giants’ walls to communicate with whomever they please. The Tech Giants don’t own the standard messaging protocols and they don’t own you.
-
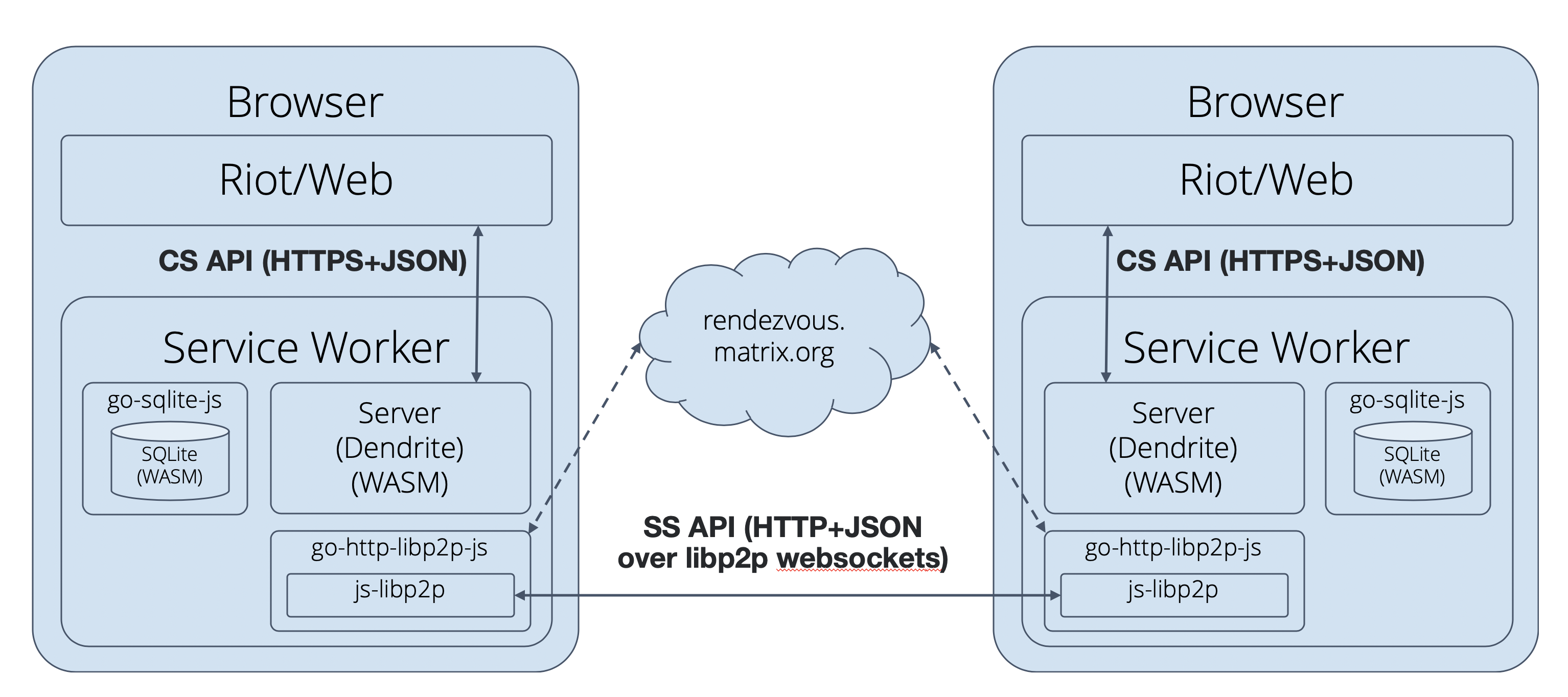
Introducing P2P Matrix
Matrix launched a Peer to Peer framework this year to further protect user’s data and give them absolute total autonomy and ownership of their secure conversations.
-

Introducing the Pinecone overlay network
The Matrix Foundation is adapting their P2P framework to incorporate global spanning tree ideas from Yggdrasil with a modified keyed routing mechanism which they adorably named SNEK, intending to integrate their protocols into IPFS.
-

Best Password Manager to use in 2021
If keeping track of all of your passwords is driving you nuts, you need a password manager. For the technically savvy: use your own bitwarden server. If that’s not an option, checkout this article on the best password managers.
-

GitHub Actions check-spelling community workflow - GITHUB_TOKEN leakage via advice.txt symlink
Security alert! GitHub Action’s community workflow spellchecker is exploitable, allowing fulldumps of repo environment variables. Vulnerable assets include temporary tokens, giving attackers all the permissions needed to execute supply-chain attacks.
-

OpenSSL3.0 Has Been Released!
Having huge changes, new features, and deprecated APIs, OpenSSL 3.0 will not be backwards compatible. Temporarily, most programs will work correctly despite depreciation warnings - though those APIs will need migration in the future.
-

Element's latest bridge for Matrix: 'All the good stuff from WhatsApp, without the less good Facebook stuff'
Like your secret tunnel through the Tech Giant’s gulag walls, Element incorporates WhatsApp into it’s cross-platform Matrix framework, allowing encrypted cross platform communications and interactions.
We took a hard look at Google this week after reading a great article from Cyrus Shepard over at Zyppy. Alphabet’s indefatigable absorption of the internet through Google is always worth careful attention. This week though we’re also highlighting some database pieces and a wonderful resource that compares how well different programming languages handle standardized problems.
-

Twitter now requiring login to view tweets
DataHoarder users are expressing their annoyance and distrust at Twitter, which is beginning to require users login to view tweets. Given Twitter’s many other data-ethics issues, what should be a minor annoyance compounds into a big issue.
-
Googlespeak – How Google Limits Thought About Antitrust
Public enemy no.1 is breaking containment. SEO proprietor Cyrus Shepard explains how Google stifles antitrust suits with “Googlespeak”. Can this dystopian future be stopped before Google IS the internet and all of humanity is either a user or partner?
-

Nitter: Alternative Twitter Front-End
Nitter is an alternative Front-End for Twitter that rips off and tosses Twitter’s front-end, insulating your device from whatever new “creepy uncle” licenses Twitter decided it wants to take with your data this week.
-
How Discord Stores Billions of Messages (2017)
Fascinating. Ever wonder how Discord handles the 100 million+ messages its users create every day? Here’s a look into the hardware infrastructure, software architecture, and data modeling that Discord uses to efficiently store and retrieve that data glut.
This week we cast a wide net, pulling in news on a variety of topics. We’ve got you covered with topics ranging from automation, data, models, and hardware developments to Twitter and WhatsApp policy. We even make a stop for motivation.
Remember where you’re going matters more than where you are. Pay attention to your trajectory.
-

Did America Just Lose Afghanistan Because of WhatsApp?
Interesting article about the Taliban’s use of the decentralized communication platform WhatsApp to coordinate both their propaganda and their operations as they toppled the Afghan government. Followed with speculation for what this may mean domestically.
-

Congressman: Yes We Did In Fact Lose Afghanistan Because of Big Tech
A shorter follow-up to Preston Byrnes’ previous article which argues tech centralization and monopolization is to blame, not Section 230. Or rather, that Section 230 is being ignored by vertical monopolies in the tech sector which should be broken up.
-
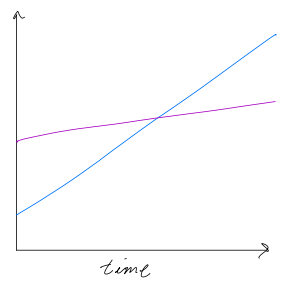
Hire for Slope, not Y-Intercept
Remember: trajectory is more important than position. Reaching your ideals means you should dream bigger. Ideals aren’t intended to be reached, rather they reveal where you can still improve. Tell yourself the truth and the truth will set you free.
-

It’s Time to Retire the CSV
The Good: There are problems with the Comma Separated Values format, such as ambiguity, prevalent alt-formats and lack of metadata- The Bad: this ignores the necessity of a universal data-export format and almost reads like ‘Critical Data Theory’
This week we’ve got plenty on security, infrastructure, organization and decentralization. The information age goes both ways. Stay safe out there boys and girls.
-

Data: What is DevSecOps?
What is DevSecOps? Interesting tweak on the DevOps model. Security baked directly into the process, rather than left as a new-development concern.
-

Six Paths to Mitigating Application Security Risks
Few things are more important to your operations than the health of your DevOps Pipelines and Enterprise Applications Infrastructure. This article teaches how to defend this critical infrastructure.
-

OpenSSL security advisory (2021-08-24)
OpenSSL reports discovery of two new security flaws, both buffer overflows, affecting OpenSSL versions 1.1.1k, 1.0.1, 1.0.2y and 3.0 alpha/beta. OpenSSL recommends users update to supported builds 1.1.1l, 1.0.2za. Upcoming security patches for 3.0.
-

How to Develop Your Business' Technology Roadmap
Here’s an overview of Technology Roadmaps and Agile followed with the tips and tricks necessary to make it happen. Includes an 8 step plan for developing and integrating a Business’’’ Technology Roadmap.
As part of a new blog series, every week we’ll gather the tech news and resources across the web our staff here at DBA finds most interesting, cool, important, or useful and new them here every Friday. Stay tuned for your weekly Tech Rundown.
-
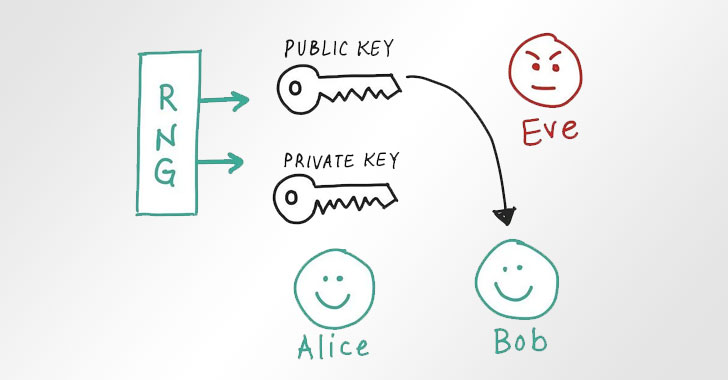
A Critical Random Number Generator Flaw Affects Billions of IOT Devices
Billions of IOT devices generate random numbers for security using non-varied seeds. Apparently, they are vulnerable to a single point of failure, where the entropy dries up and simple keys are generated.
-

Manufacturing Tech Orders on the Rise
Q1 winddown of covid-19 hysteria credited with a massive increase in manufacturing technology orders. Gains spread throughout manufacturing industries, notably medical and humble hardware domestic production.
-

Valve's upcoming Steam Deck Will be Based on Arch, not Debian
Valve shifts the Linux distro on its upcoming portable hardware from Debian to the Arch. Interesting speculation and indication of a change in design philosophy.